forked from acouzens/open5gs
Add PCAP analysis to successful calls (#413)
* Adopt tutorial format to dockerized VoLTE lab * Fixed several lines according to Supreeth's feedback * add PCAP analysis to successful calls
This commit is contained in:
parent
c00f67caab
commit
713693ee78
|
|
@ -191,6 +191,49 @@ The successful calls were made with a commercial eNB (in his case a Casa
|
|||
smallcell), while srsENB the ACK takes a very long time to reach the UE,
|
||||
resulting in disconnected calls.
|
||||
|
||||
**UE registration**
|
||||
|
||||
|
||||
|
||||
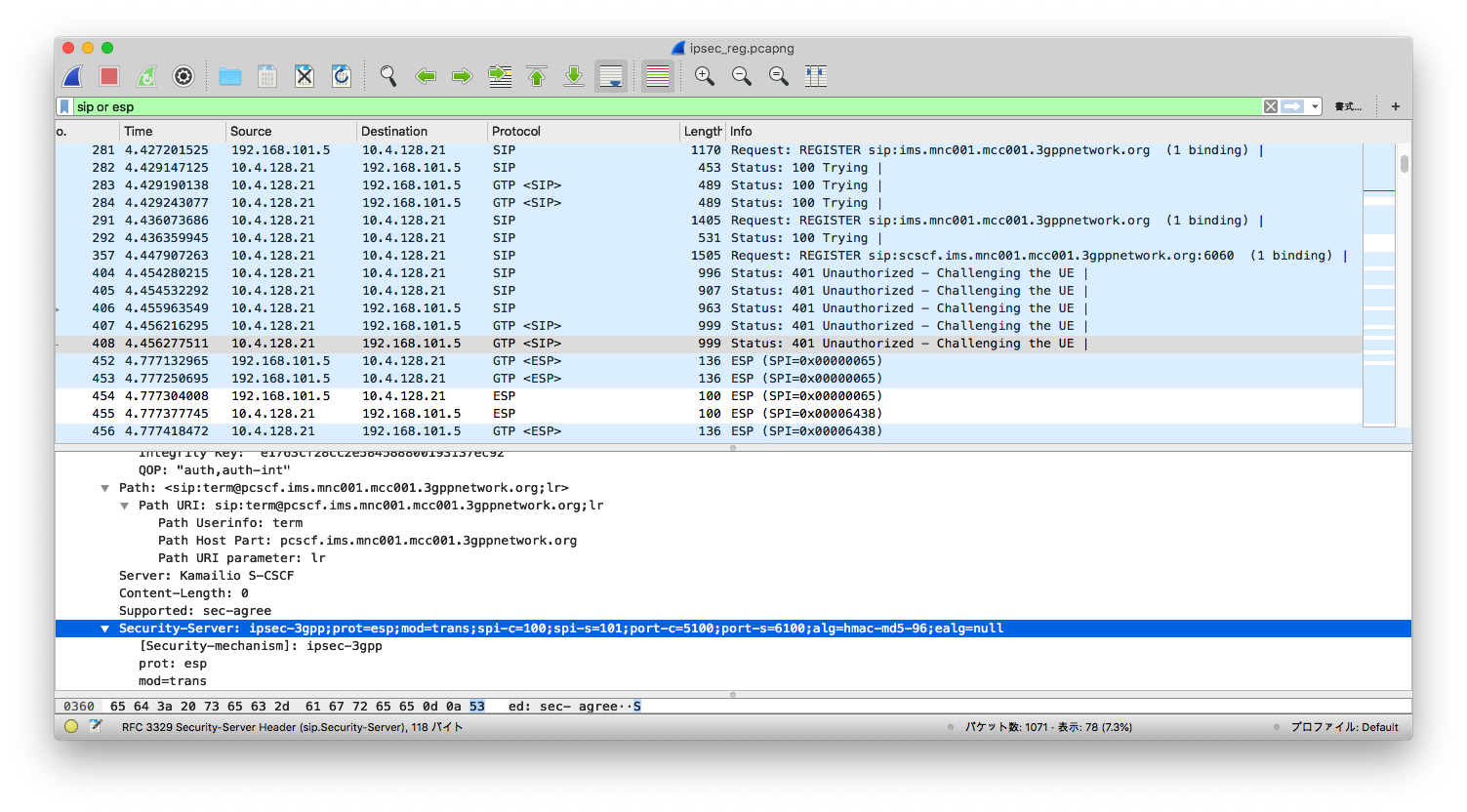
From the screenshot, we see a UE that supports IPSec got a response from
|
||||
S-CSCF, indicating that ipsec-3gpp is supported, protocol is ESP (ethernet
|
||||
proto 50, IPSec). Client port (port-c) is 5100 and server port (port-s) 6100.
|
||||
Refer to [IMS/SIP - Basic Procedures](https://www.sharetechnote.com/html/IMS_SIP_Procedure_Reg_Auth_IPSec.html) if you want to know more.
|
||||
Also, notice that packets after 401 Unauthorized are transmitted over ESP.
|
||||
|
||||
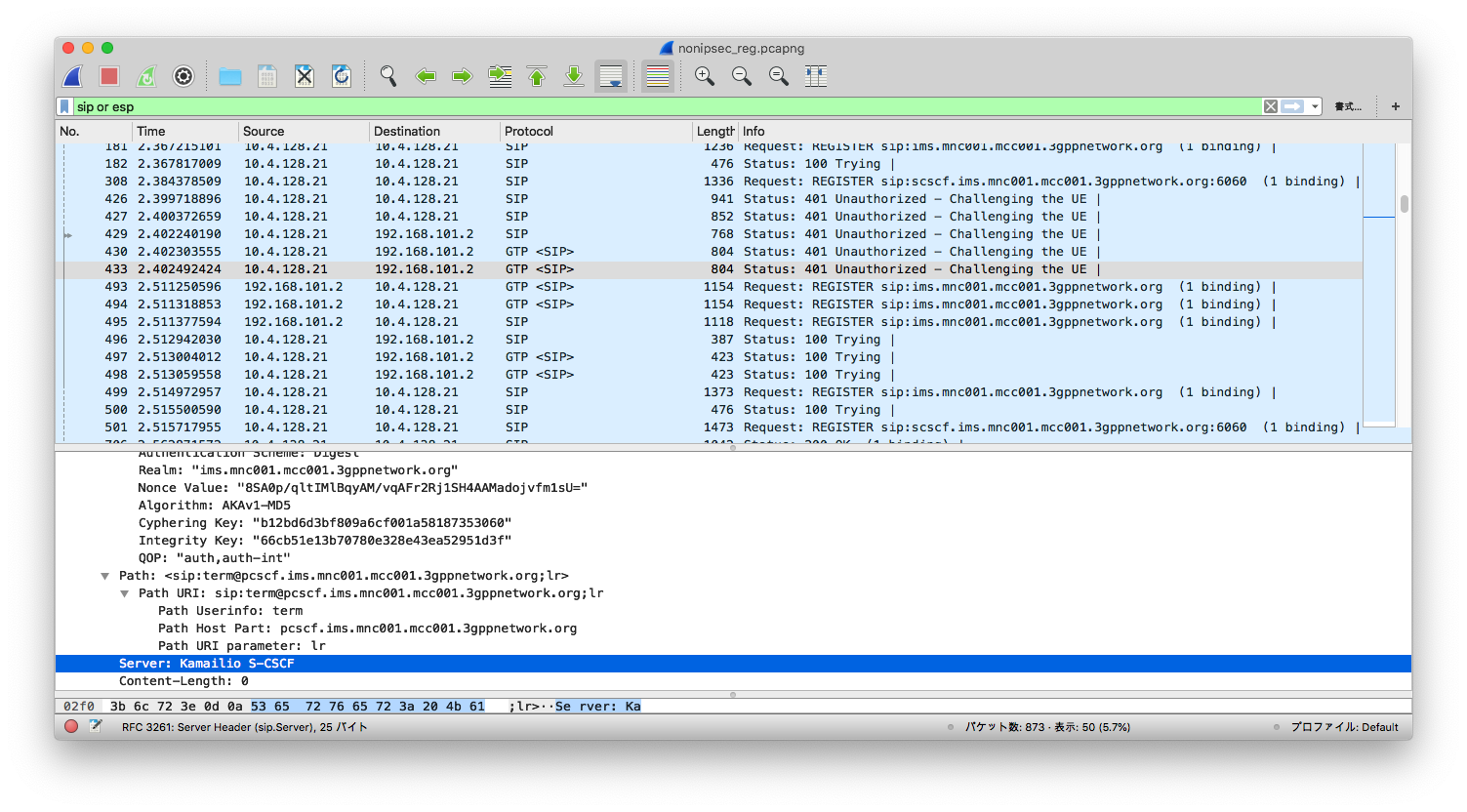
If a UE does not support IPSec, you don't see the "security-server", as shown below:
|
||||
|
||||
|
||||
|
||||
|
||||
**VoLTE calls**
|
||||
|
||||
|
||||
|
||||
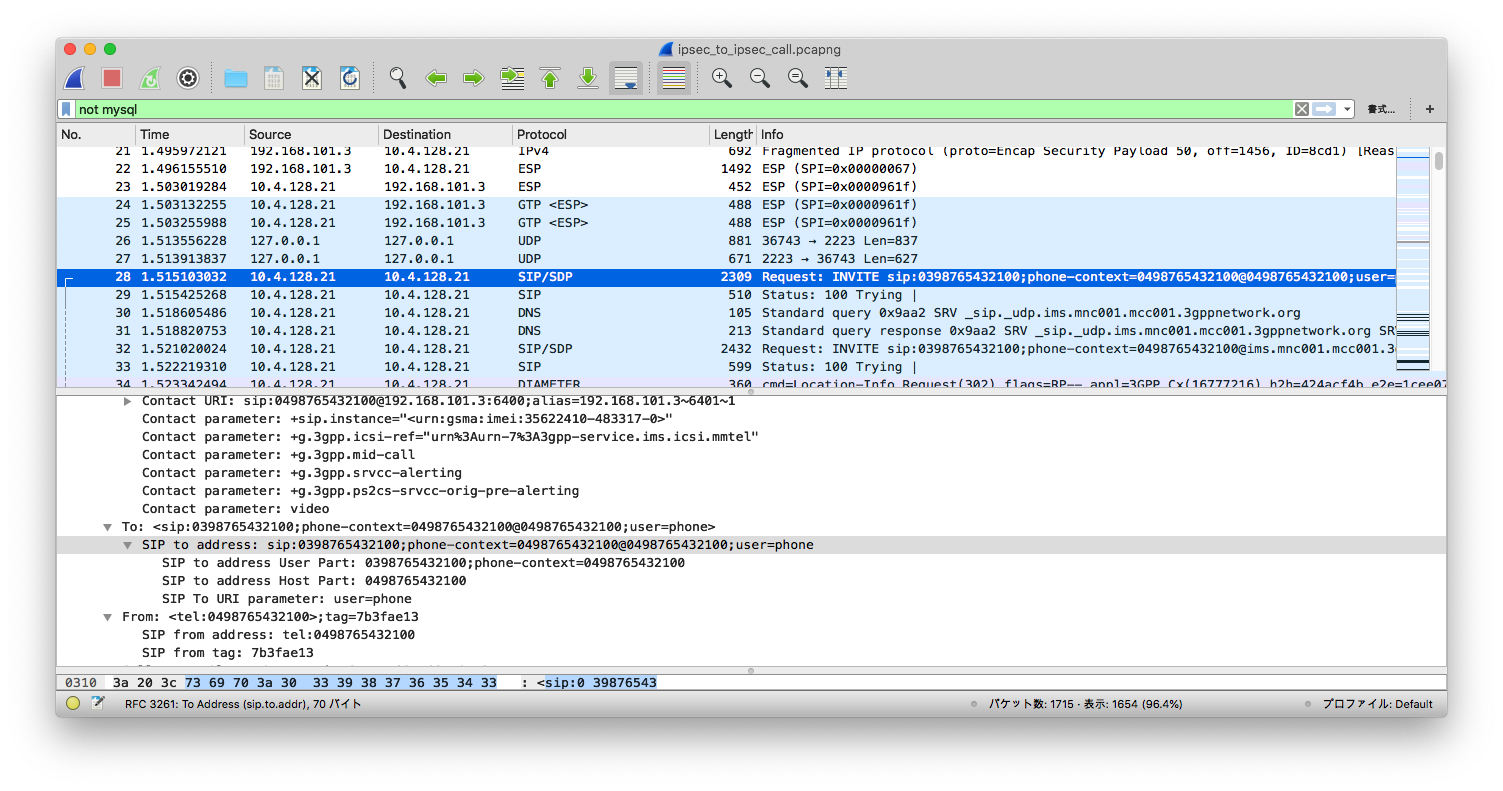
The Wireshark above shows that after several IPSec (ESP) packets, S-CSCF is
|
||||
sending a SIP INVITE for UE 03 to UE 04. To be more precise,
|
||||
|
||||
```
|
||||
Request-Line: INVITE sip:0398765432100;phone-context=0498765432100@0498765432100;user=phone SIP/2.0
|
||||
...
|
||||
Record-Route URI: sip:mo@10.4.128.21:6101;lr=on;ftag=7b3fae13;rm=8;did=078.654
|
||||
```
|
||||
|
||||
The SIP port of the caller (`contact`) will also be passed to the callee,
|
||||
```
|
||||
Contact URI: sip:0498765432100@192.168.101.3:6400;alias=192.168.101.3~6401~1
|
||||
```
|
||||
|
||||
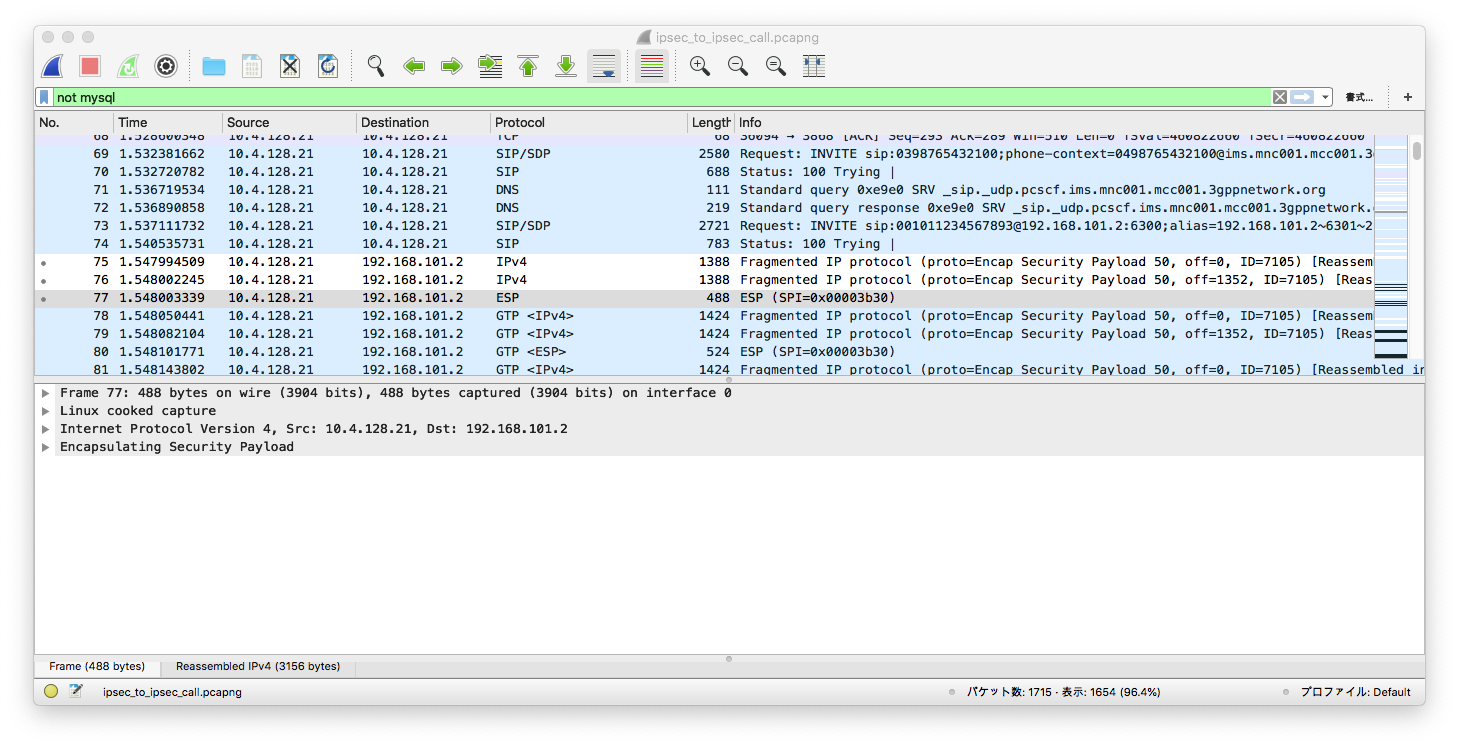
After S-CSCF forwarded the INVITE to P-CSCF, it returns a 100 Trying, and contacts with the callee via IPSec:
|
||||
|
||||
|
||||
|
||||
This can be contrasted when the callee does not support IPSec. After 100
|
||||
Trying, a UE that does not support IPSec is sent a SIP INVITE in clear text:
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
#### 7. Known issues
|
||||
|
||||
|
|
|
|||
Loading…
Reference in New Issue